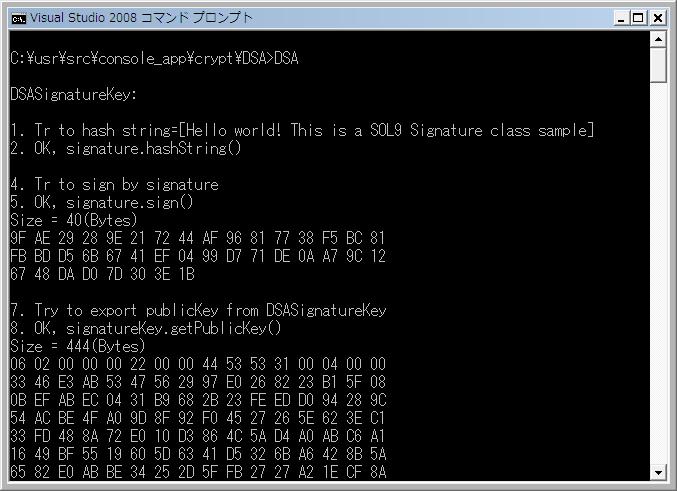
1 Screenshot
2 Source code
/*
* DSA.cpp
* Copyright (c) 2015 Antillia.com TOSHIYUKI ARAI. ALL RIGHTS RESERVED.
*/
// 2009/03/03
#include <sol/crypt/DSACryptServiceProvider.h>
#include <sol/crypt/DSASignatureKey.h>
#include <sol/crypt/Signature.h>
void cryptError()
{
const TCHAR* msg = CryptError::getMessage(GetLastError());
_tprintf(_T("%s\n"), msg);
}
int _tmain(int argc, TCHAR** argv)
{
int rc = 0;
try {
//Specify DSACryptServiceProvider of named container.
DSACryptServiceProvider csp(_T("TEST"));
{
_tprintf(_T("\nDSASignatureKey:\n"));
// Specify CALG_SHA1 not CALG_MD5.
Signature signature(csp, CALG_SHA1);
const char* message = "Hello world! This is a SOL9 Signature class sample";
_tprintf(_T("\n1. Tr to hash string=[%s]\n"), message);
if (signature.hashString(message) == NO_ERROR) {
_tprintf(_T("2. OK, signature.hashString()\n"));
} else {
_tprintf(_T("3. Failed in signature.hashString()\n"));
cryptError();
}
_tprintf(_T("\n4. Tr to sign by signature\n"));
Bytes signedBytes;
if (signature.sign(signedBytes) ==NO_ERROR) {
_tprintf(_T("5. OK, signature.sign()\n"));
signedBytes.dump();
} else {
_tprintf(_T("6. Failed in signature.sign()\n"));
cryptError();
}
DSASignatureKey signatureKey(csp);
//
_tprintf(_T("\n7. Try to export publicKey from DSASignatureKey\n"));
Bytes pubKey;
if (signatureKey.getPublicKey(pubKey) == NO_ERROR) {
_tprintf(_T("8. OK, signatureKey.getPublicKey()\n"));
pubKey.dump();
} else {
_tprintf(_T("9. Failed in signatureKey.getPublicKey()\n"));
cryptError();
}
_tprintf(_T("\n10. Try to export privateKey from signatureKey\n"));
//
Bytes priKey;
if (signatureKey.getPrivateKey(priKey) == NO_ERROR) {
_tprintf(_T("11. OK signatureKey.getPrivateKey()\n"));
priKey.dump();
} else {
_tprintf(_T("12. Failed in signatureKey.getPrivateKey()\n"));
cryptError();
}
_tprintf(_T("\n13. Try to import pubKey \n"));
CryptKey impPublicKey;
if (impPublicKey.importKey(csp.getProviderHandle(), pubKey) ==NO_ERROR) {
_tprintf(_T("14. OK, imported publicKey\n"));
} else {
_tprintf(_T("15. Failed in impPublicKey.import()\n"));
cryptError();
}
//
_tprintf(_T("\n16. Try to verify a signature by importedPublicKey\n"));
if (signature.verify(impPublicKey.getKeyHandle(), signedBytes) == NO_ERROR) {
_tprintf(_T("17. OK signature.verify()\n"));
} else {
_tprintf(_T("18. Failed in signature.verify()\n"));
cryptError();
}
}
} catch (Exception& ex) {
printf("Exception = %s\n", ex.getErrorMessage());
}
rc = GetLastError();
return rc;
}
Last modified: 2 May 2016
Copyright (c) 2016 Antillia.com ALL RIGHTS RESERVED.
